Friday, 21 March 2014
Labels:
Cyber News
Read More
Microsoft sells your Information to FBI; Syrian Electronic Army leaks Invoices
Till now we all were aware about the truth that tech companies gave legal access to user data on the government's request, but we were unaware that well known tech companies also charge the government for providing data.
Syrian Electronic Army (SEA), the pro-hacker group, who had compromised Microsoft's Twitter account and blog, earlier this year and Microsoft did announce a breach on its blog earlier this year. "It appears that documents associated with law enforcement inquiries were stolen,".
It seems that they have achieved something bigger than we expected by once more targeting Microsoft.
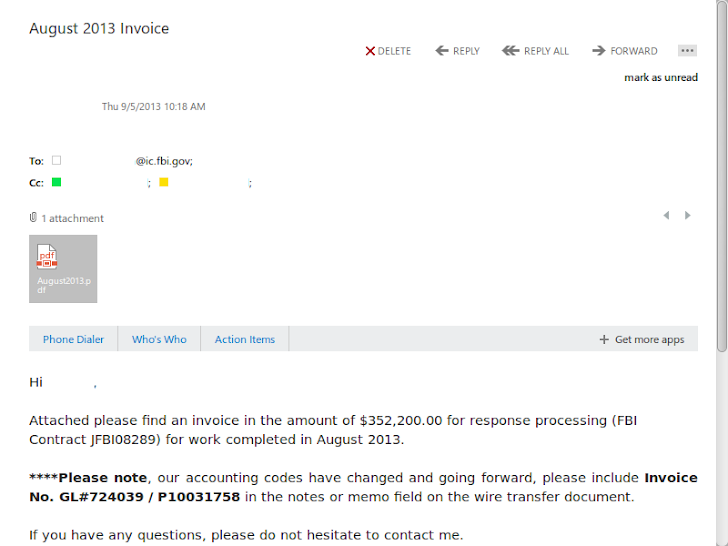
This time the SEA hacking group has managed to successfully get into the FBI's super-secret Digital Intercept Technology Unit (DITU), where they found the actual invoices from Microsoft; detailing how much each request for data cost, which means that the company charges for every document they provide to the FBI agents, Daily Dot reported.
The invoices above shows that Microsoft charged the DITU $145,100 in December 2012, at a rate of $100 per data request. In August 2013, the per-request rate increased to $200 and the latest Invoice dated November 2013, showed a charge of $281,000.
These documents show how frequently the government calls on tech companies for information and could be possible that Microsoft isn't the only company that charges the government for compliance with data requests.
The group aligned with president Bashar al-Assad, is popular for targeting western countries and media and had victimized various high-profile brands and VIPs’ twitter accounts and websites, like Forbes, Obama, Facebook, CNN, eBay and PayPal in the past using phishing techniques, and recently claimed to compromise central repository of US central command (CENTCOM).
Thursday, 20 March 2014
Labels:
Cyber News

Read More
Google Glass malware developed by researchers
Google Glass malware developed by researchers
Forbes reports that two grad students at California Polytechnic San Luis Obispo recently developed POC spyware for Google Glass ).
Malware has been desighned by Mike Lady 22 year old researcher along with Kim Paterson 24 year old software professional , malware is able to take and upload photo every 10 seconds, without knowing a user.
Paterson said:- "The scary thing for us is that while it’s a policy that you can’t turn off the display when you use the camera, there’s nothing that actually prevents you from doing it,As someone who owns Glass and wants to install more apps, I’d feel a lot better if it were simply impossible to do that. Policies don’t really protect us."
Wednesday, 19 March 2014
Labels:
Cyber News
German Car Manufacture Company namely Citroen got hacked by some Unknown hackers,Hackers had planted a "Phishing Page" at shop.citroen.de inorder to get customers data and which lead to DATA COMPROMISATION.The Car makers have confirmed the "USER DATA COMPROMISE" occurs,but it’s uncount in how many quantity of CUSTOMERS are impacted.
Alex Holden of Hold Security has investigated the breach.The backdoor is now successfully removed according to there officials that backdoor was planted since 2013.
Hackers exploited Adobe Coldfusion vulnerability to get access on the server and customers data,
other renown website which are exploited by the same vulnerability in past were Smucker and SecurePay.
Source : http://www.whogothacked.com/2014/03/citroen-gets-hacked-customer.html
Read More
Citroen Deutschland Hacked Users Data Compromised
German Car Manufacture Company namely Citroen got hacked by some Unknown hackers,Hackers had planted a "Phishing Page" at shop.citroen.de inorder to get customers data and which lead to DATA COMPROMISATION.The Car makers have confirmed the "USER DATA COMPROMISE" occurs,but it’s uncount in how many quantity of CUSTOMERS are impacted.
Alex Holden of Hold Security has investigated the breach.The backdoor is now successfully removed according to there officials that backdoor was planted since 2013.
Hackers exploited Adobe Coldfusion vulnerability to get access on the server and customers data,
other renown website which are exploited by the same vulnerability in past were Smucker and SecurePay.
Source : http://www.whogothacked.com/2014/03/citroen-gets-hacked-customer.html
Tuesday, 18 March 2014
Labels:
Tutorials
Read More
Hacking Facebook User 'Access Token' with Man-in-the-Middle Attack
Facebook has several security measures to protect users' account, such as a user "access token" is granted to the Facebook application (like Candy Crush Saga, Lexulous Word Game), when the user authorizes it, it provides temporary and secure access to Facebook APIs.
To make this possible, users have to 'allow or accept' the application request so that an app can access your account information with the required permissions.
The Access Token stores information about permissions that have been granted as well as information about when the token will expire and which app generated it. Approved Facebook apps can publish or delete content on your behalf using the access tokens, rather than your Facebook password.
Access tokens are pretty sensitive, because anyone who knows the access token of a user can access the user's data and can perform any actions on behalf of the user, till the token is valid.
In Past years, Many Security Researchers reported various Oauth vulnerabilities to the Facebook Security team, but if the app traffic is not encrypted, you are not protected from the man-in-the middle attack and the attacker could steal your private information, using 'access token'.
Thus, access token is enough to allow a hacker to do all that the app authorized to do. The vulnerability is not new, it has already been known for a year, but Facebook is still vulnerable to hackers and surveillance specialized agencies like the NSA.
FACBOOK CAN'T FIX IT: The Facebook Security team has acknowledged the vulnerability claimed by Ahmed Elsobky, a penetration tester from Egypt, "We'd actually received an earlier report from another researcher regarding this same issue. In response to that report, we've been working on limiting this behavior when it comes to our official apps, since they're pre-authorized. For other apps, unfortunately, fully preventing this would mean requiring any site integrating with Facebook to use HTTPS, which simply isn't practical for right now."
He demonstrated that 'How to hack a Facebook account by hijacking access token with Man-in-the-Middle attack', as shown:
Facebook apps must be protected from man-in-the middle attacks, and this can be done effectively by using HTTPS to encrypt any traffic that contains sensitive information or authentication credentials...
HOW TO PROTECT YOUR ACCOUNT: If You are a Facebook app developer, you should never send an 'access token' over unencrypted channels and Facebook users should only trust the encrypted apps and use "HTTPS Everywhere" Browser Extension for automated security...
Monday, 17 March 2014
Labels:
Cyber News
# Pakistan Zindabad
Read More
TOYOTA & RENAULT & CHEVROLET Guatemala Hacked
TOYOTA & RENAULT & CHEVROLET Guatemala Hacked
# Hacked By Team Cyber Criminals
# Pakistan Zindabad
http://www.chevrolet.com.gt/
http://www.renault.com.gt/
http://www.toyota.com.gt/
Hacked By Team Cyber Criminals
mirrors;
http://zone-h.com/mirror/id/22028173
http://zone-h.com/mirror/id/22028170
http://zone-h.com/mirror/id/22025495
Pakistani Team..
Subscribe to:
Comments
(
Atom
)