Monday, 24 March 2014
Labels:
Cyber News
Read More
A New Open Source Programming Language developed by Facebook
Facebook just released a new programming language called 'HACK', designed to build complex websites and other software quickly and without many flaws. The company has already migrated almost all of its PHP-based social networking site to HACK over the last year, but it has nothing to do with Hacking.
When Social Networking website Facebook was started 10 years ago, it was coded in PHP by Mark Zuckerberg and team, but as the company grew, PHP Programming platform became difficult to manage and bug-free.
Thus, Hack was born! Facebook Team decides to develop a new programming language that could combine elements of static-type programming languages such as C or C++ with dynamic-type languages like PHP, now called "HACK Programming Language".
"Hack has deep roots in PHP. In fact, most PHP files are already valid Hack files." Facebook said, "We have also added many new features that we believe will help make developers more productive."
HACK is a new version of PHP, requires Facebook’s HHVM (Hip Hop Virtual Machine) which is designed to execute programs written in Hack and PHP. The top 20 open source frameworks on Github run on HHVM.
"Traditionally, dynamically typed languages allow for rapid development, but sacrifice the ability to catch errors early and introspect code quickly, particularly on larger codebases." Facebook posted on itsengineering blog.
So Hack Programming Language offers a lot of potential for developers, enabling them to program faster and be able to catch errors more easily, among other things. "Conversely, statically typed languages provide more of a safety net, but often at the cost of quick iteration. We believed there had to be a sweet spot."
Beta code is open source and now available at Hacklang.org and you can also get Hack programming language tutorials from website to learn this new language. ...
"This is just the first step, and we are dedicated to continuing to evolve this software to make development even easier for both our own engineers and the broader community." The public release is not just to encourage developers, but also to quickly spot errors in Hack....
Sunday, 23 March 2014
Labels:
Cyber News

Read More
NSA Hacked Servers of Chinese telecom Huawei, Stole Source Codes.

The US Government was publicly accusing Chinese electronics manufacturer Huawei of espionage from the past few years.
Ironically, it has now been revealed that the National Security Agency conducted a major offensive cyber operations against the Chinese government and networking company Huawei, in early 2009.
According to reports based on classified documents leaked by Edward Snowden and viewed by The Times and Der Spiegel, NSA has infiltrated servers in the headquarters of Chinese telecommunications and hacked into the email servers of Huawei five years ago.
Code-named as "Operation Shotgiant" was conducted with the involvement of the CIA, White House intelligence coordinator and the FBI; aimed to find a link between Huawei and China’s People’s Liberation Army. NSA accessed the emails of many Huawei employees' for this purpose.
NSA STOLE SOURCE CODES
NSA also aimed to conduct surveillance through computer and telephone networks Huawei sold to other nations. According to the papers, NSA stole the secret source code for certain Huawei products, and obtained the information on how to exploit Huawei's products in order to spy on foreign customers such as Iran, Afghanistan, Pakistan, Kenya, and Cuba.
The reports show the NSA spying on former Chinese President Hu Jintao, the country’s trade ministry, banks, telecoms firms and also tracking more than 20 Chinese hacking groups, where more than half of them Chinese Army or Navy units.
"If it is true, the irony is that exactly what they are doing to us is what they have always charged that the Chinese are doing through us," William Plummer, a senior Huawei executive in the United States "If such espionage has been truly conducted, then it is known that the company is independent and has no unusual ties to any government and that knowledge should be relayed publicly to put an end to an era of mis- and disinformation."
NSA- 'WE HACK FOR NATIONAL SECURITY'
The US and China are hacking each other from long time and NSA spokeswoman Caitlin Hayden said that the NSA spying is for national security purposes only, "We do not give intelligence we collect to US companies to enhance their international competitiveness or increase their bottom line."
The US Government labeled their actions (Stealing Source codes, installing backdoors) as 'Hacking for National Security' and accusing Huawei for 'Corporate Theft'. In a document NSA wrote, "We currently have good access and so much data that we don't know what to do with it,"
Saturday, 22 March 2014
Labels:
Cyber News

Read More
Pileup flaw Android updates can be exploited by malware to gain permissions

Upgrading an operating system patches the security holes in the previous versions. However, researchers found a bug in upgrading process of Android itself, which can be exploited by malicious apps.
Sponsored Links
A team of researchers from Indiana University and Microsoft have published a paper explains a new critical security bugs which are referred as "Pileup flaws". The vulnerability exists in Package Management Service (PMS) of Android.
When a user upgrades android to the latest version, a malicious app with few or no permission in the old version can exploit this vulnerability to update itself with new set of permissions.
An attacker can exploit this vulnerability to steal sensitive information from the compromised device, change security configurations and also prevent installation of critical system services.
Researchers say they have confirmed the presence of security hole on all official android versions as well as 3,000 customized android versions.
Researchers also have developed a new service called 'SecUp' which is capable of detecting the malicious apps designed to exploit PileUp vulnerabilities...
Friday, 21 March 2014
Labels:
Cyber News
Read More
Scammers targeting Google Account with Phishing Page hosted on Google Drive
You all are quite aware of phishing attacks, and for those who are not, Phishing scams are typically fraudulent email messages, masquerading as a well known and trustworthy entity in an attempt to gather personal and financial information from victims. However, phishing attacks have become more sophisticated recently.
The Pro-hacker group, Syrian Electronic Army (SEA) is also popular for its advance phishing attack and had purposely targeted twitter account and websites of various popular brands like Forbes, Microsoft, Obama, Facebook, CNN, eBay and PayPal in the past using phishing techniques.
Security researchers have seen an increase in the number of phishing attacks every day, but recently a tricky scam came across by the researchers at the Symantec, which is targeting Google Docs and Google Drive users.
Under this phishing scam, an email with a subject of "Documents", tricks recipient to view an ‘important document’ stored on the Google Docs by clicking the included link in the email. But supposed to be directed to important Google doc, the user is redirected to a fake login page, where he is required to enter his Google account information, i.e. Username and Password.
One just needs to create a folder on Google Drive to host the phishing site, so it shows the address bar of the browser to “google.com” and let the fake login page run on the preview function of Docs. This allows criminals to make use of SSL encryption of Google, to deceive the victim further.
"The fake page is actually hosted on Google's servers and is served over SSL, making the page even more convincing," Symantec security expert Nick Johnston explained. "The scammers have simply created a folder inside a Google Drive account, marked it as public, uploaded a file there, and then used Google Drive's preview feature to get a publicly accessible URL to include in their messages."
It's really very common for the users to be prompted with a login page like this when accessing a Google Docs link and many of us may enter our credentials without a second thought. But, as soon as you enter the information and press "Sign in" button, a compromised web server with PHP script will receive and store your stolen credentials.
“This page then redirects to a real Google Docs document, making the whole attack very convincing. Google accounts are a valuable target for phishers, as they can be used to access many services including Gmail and Google Play, which can be used to purchase Android applications and content,” Johnston explained.
It is always recommended to login to any of your online accounts by entering the address into your browser's address bar rather than clicking a link in an unsolicited email and when any service required your login, have a close look that whether the request to click the link really makes sense or not.
Labels:
Cyber News
Read More
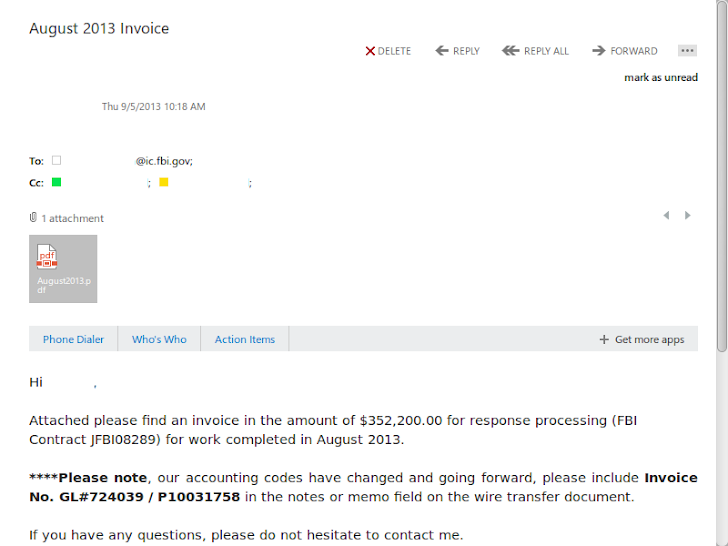
Microsoft sells your Information to FBI; Syrian Electronic Army leaks Invoices
Till now we all were aware about the truth that tech companies gave legal access to user data on the government's request, but we were unaware that well known tech companies also charge the government for providing data.
Syrian Electronic Army (SEA), the pro-hacker group, who had compromised Microsoft's Twitter account and blog, earlier this year and Microsoft did announce a breach on its blog earlier this year. "It appears that documents associated with law enforcement inquiries were stolen,".
It seems that they have achieved something bigger than we expected by once more targeting Microsoft.
This time the SEA hacking group has managed to successfully get into the FBI's super-secret Digital Intercept Technology Unit (DITU), where they found the actual invoices from Microsoft; detailing how much each request for data cost, which means that the company charges for every document they provide to the FBI agents, Daily Dot reported.
The invoices above shows that Microsoft charged the DITU $145,100 in December 2012, at a rate of $100 per data request. In August 2013, the per-request rate increased to $200 and the latest Invoice dated November 2013, showed a charge of $281,000.
These documents show how frequently the government calls on tech companies for information and could be possible that Microsoft isn't the only company that charges the government for compliance with data requests.
The group aligned with president Bashar al-Assad, is popular for targeting western countries and media and had victimized various high-profile brands and VIPs’ twitter accounts and websites, like Forbes, Obama, Facebook, CNN, eBay and PayPal in the past using phishing techniques, and recently claimed to compromise central repository of US central command (CENTCOM).
Subscribe to:
Comments
(
Atom
)